Threat-Centric Approaches No Longer Enough, Companies Need to Adopt an Access-Centric Cybersecurity Strategy
For so long, organisations have been used to negotiating their security landscape in a reactive way. Meaning, they tend to focus on addressing threats or vulnerabilities once detected or even isolating their systems to mitigate attacks. This may work in the old setting where sensitive data and processes are only confined within internal networks. However, the cloud and digital transformation, further accelerated by the pandemic, has changed all this.
Now, cyber attacks can come from anywhere as businesses operate using various remote endpoints, going beyond their established perimeters. Rani Nathwani, PIKOM CIO Chapter Chairperson, said that it is no longer a question of if your organisation will be attacked but a question of when, during yesterday’s virtual event held by IBM and PIKOM, which focused on helping businesses “Build a Stronger Defence Against Cyber Attacks.”

“As experts in cybersecurity, we always strive to keep our people safe. We understand now that we need to evolve, our security framework needs to address the failures of the existing parameter-based security approaches,” Rani added.
To talk more about how organisations can do this, Rani handed the discussion over to Rajesh Baronia, Digital Trust Technical Leader, IBM Asia Pacific, who spoke on how the zero-trust approach can enable organisations to “secure in a transforming world”.
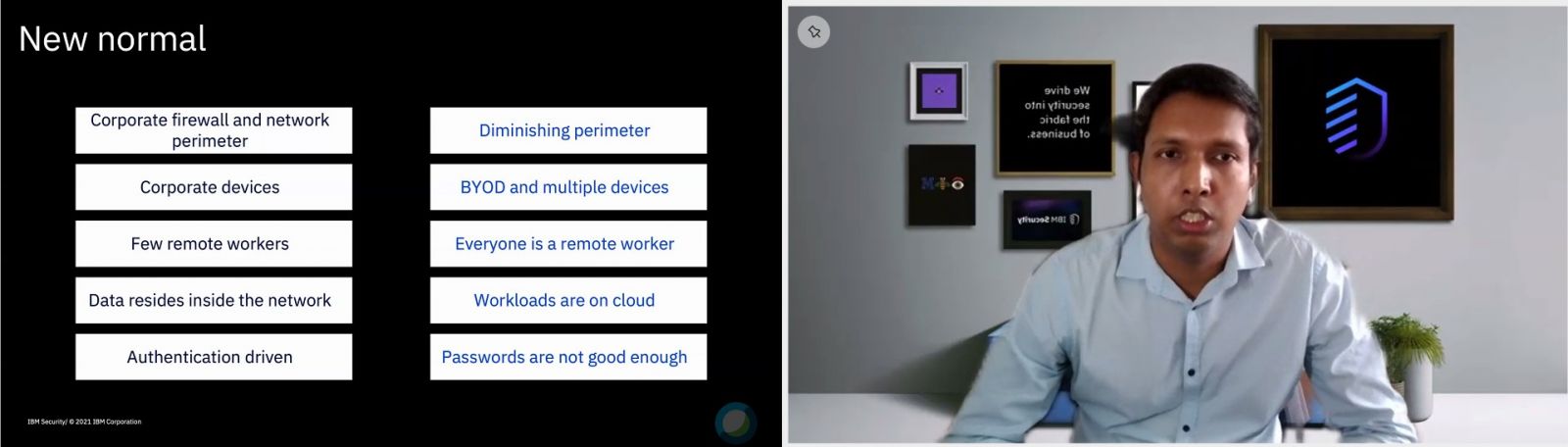
Rajesh started his session by saying that a parameter-based defence, long accepted as the traditional IT security model, has been under siege for many years now. This is especially true in today’s highly volatile and unpredictable cyber landscape, which presents greater risk as well as a unique opportunity for security leaders to rethink and reinforce organisation defences.
For example, Rajesh explained that while businesses used to operate mainly within a corporate firewall, this perimeter is now diminishing. In the “new normal”, especially, remote workers are increasingly being prioritised. These typically consist of employees and even external parties who utilise their own devices instead of corporate-issued ones. In addition, more workloads and data are now on the cloud, with access expanding to new IT environments.
“The traditional security of trusting and then verifying the user has serious gaps in the current situation, where we have seen security from a threat-centric perspective. What is needed in the new normal, however, is security that is more dynamic in nature,” explained Rajesh.
Embracing the ‘Never Trust, Always Verify’ Mantra
For Rajesh, organisations need to change from the current threat-centric approach to an access-centric approach where every access attempt is evaluated based on its own merit, enabling the right users under the right conditions to have the right access to the right data.
This is what a zero-trust approach is all about, focusing on four principles: implement least privilege, assume breach, eliminate perimeter-based controls and never trust, always verify. “Zero-trust is not a single product, it's not a single solution. It's an approach, it's a mindset. It's a cultural shift for you as an organisation and to be successful with this approach, what you need is an open platform to leverage on your technology investments and with necessarily no vendor locking,” explained Rajesh.
With that, Rajesh mentioned that IBM delivers zero-trust expertise, integrated products and services on an extended partner ecosystem, with a demonstration of how the approach works using personas that include a remote worker, the CIO and a threat actor. IBM works in three aspects for their zero-trust approach, namely:
-
Insights: Discover and access risk across data, identity, endpoint, app and infrastructure with IBM Security Guardium.
-
Enforcement: Context-aware access control to all apps, data, APIs, endpoints and hybrid cloud services with IBM Security Verify Access.
-
Detection and Response: Identify risks and automate responses that dynamically adapt access controls with IBM Cloud Pak for Security.
At the end of the session, representatives from managed security services firm and IBM partner, LifeTech Group, had a demonstration where they showed some of the tools, technologies and techniques required in the day-to-day operations of a managed SOC in dealing with modern cyber threats. In particular, they focused on how the IBM QRadar Security Intelligence Platform, a data-driven Security Information and Event Management (SIEM) solution, can be used to address a problem such as brute force attacks that are often carried out by threat actors.
During the demo, Nicholas Yong, Senior Manager at LifeTech Group, explained how most organisations over the years concentrate on preventing external parties from entering their environments, investing in things like firewalls, Endpoint Detection and Response (EDR) and other such solutions. He then showed how cybercriminals can circumvent such approaches by gaining insider access to carry out more effective and devastating attacks.
Nicholas highlighted the need for businesses to rethink how they secure their systems and adopt a more comprehensive approach like zero-trust. Otherwise, they are leaving themselves exposed and will quickly be overwhelmed by the number of threats they will continue to face on a daily basis.
In addressing this problem, he said managed security services companies such as LifeTech can offer not only detection and prevention capabilities but also monitoring tools up to the server level – server logs, audit logs as well as the routers and network switches.
In addition, LifeTech has adopted technologies such as AI to make their solutions more responsive, essentially making them a cognitive Security Operations Centre (SOC). This is important in a zero-trust approach, where organisations need to regulate access across their extensive IT environment without compromising the experience of their workforce.












_0.jpg)

0 Comment Log in or register to post comments